The Cybersecurity Problem
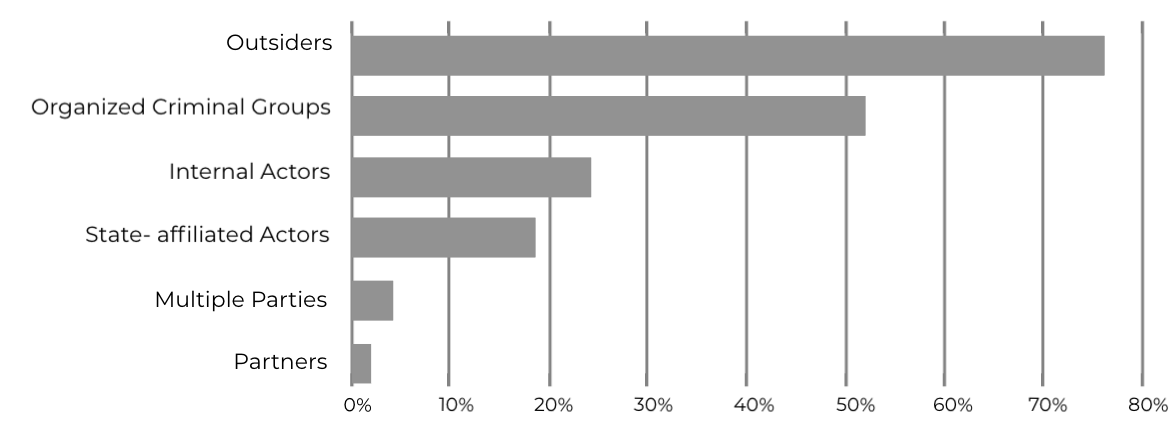
Who Causes the Cybersecurity Problem?
Begin by thinking about the most crucial elements of your business. How are you using IT to achieve business outcomes? What dependencies, including your Supply Chain, do you have to achieve those outcomes? How complete and current is your Business Impact Analysis.
Key Concepts for Cybersecurity: Build a Framework
Confidentiality. Integrity. Availability.
This is the fine balancing act for Cybersecurity, also know as the “bedrock principle for Cybersecurity.” There’s no such thing as perfect security, you can’t spend all resources on all three areas – so focusing on the business, and identifying which of these are important to the business units help properly align Cybersecurity solutions with business outcomes.
People. Process. Technology.
This is the crux of a solid Cybersecurity program. Buying a solid technology solution alone will not address Cybersecurity. You need the right people, with the right expertise, governed by the right processes to effectively manage Cybersecurity. If you don’t have this internally, leverage consultants to build a program around this, or buy it “as a service” from excellent Managed Services Firm.
Protect. Detect. Respond.
These are the critical business outcomes and capabilities of a Cybersecurity program. Organizations must have the ability to Protect, Detect, and Respond to Cyber threats. Here again, this means balance. Spending all the resources; spreading that spend across all three categories is crucial, more effective, and delivers a better Cybersecurity posture.